Why Traditional Security Operations Can’t Keep Up
As cybercriminals grow more sophisticated, traditional security struggles to keep pace. Companies take an average of 280 days to detect a breach, giving attackers ample time to steal data and cause damage. For most businesses, building an in-house Security Operations Center (SOC) is not feasible due to prohibitive costs, 24/7 staffing demands, and a severe cybersecurity skills shortage.
This is where a virtual security operations center (VSOC) comes in. A VSOC is a cloud-based, outsourced security solution providing 24/7 monitoring, threat detection, and incident response through remote teams and advanced technology. It delivers enterprise-grade security at a fraction of the cost by eliminating the need for a physical facility, on-site hardware, or a large in-house team.
Key characteristics include:
- Decentralized, remote operations using cloud platforms
- Continuous 24/7 monitoring across all time zones
- Cost-effective with no physical infrastructure costs
- Scalable to adapt to business growth
- Expert-driven with access to certified security analysts
With corporate networks seeing 50% more cyber attacks per week in recent years, the question isn’t whether you need robust security, but how you can implement it effectively. The VSOC model provides the answer.
What is a Virtual Security Operations Center (VSOC)?
A virtual security operations center is your company’s dedicated cybersecurity guardian, delivered through the cloud. Instead of a physical facility with on-site staff, a VSOC uses remote teams of security experts who monitor your digital assets around the clock from secure, cloud-based platforms. This outsourced model makes enterprise-grade protection accessible without the massive overhead of an in-house operation, democratizing high-end cybersecurity for organizations of all sizes. For more details on this service model, see our article on SOC as a Service (SOCaaS).
The decentralized nature of a VSOC also builds resilience, ensuring continuous coverage even during local disruptions. It solves the cybersecurity skills gap by providing access to a global pool of certified experts without the recruitment headaches.
Defining the VSOC Model
The VSOC model involves a team of seasoned cybersecurity professionals continuously scanning your IT environment for threats. Using sophisticated web-based platforms, they perform proactive threat detection, hunting for unusual behavior and indicators of compromise before they escalate. When a threat is found, incident response protocols are immediately activated to contain and neutralize it.
A VSOC also integrates compliance management, helping businesses meet regulations like GDPR, HIPAA, or PCI DSS by providing continuous oversight and generating necessary reports.
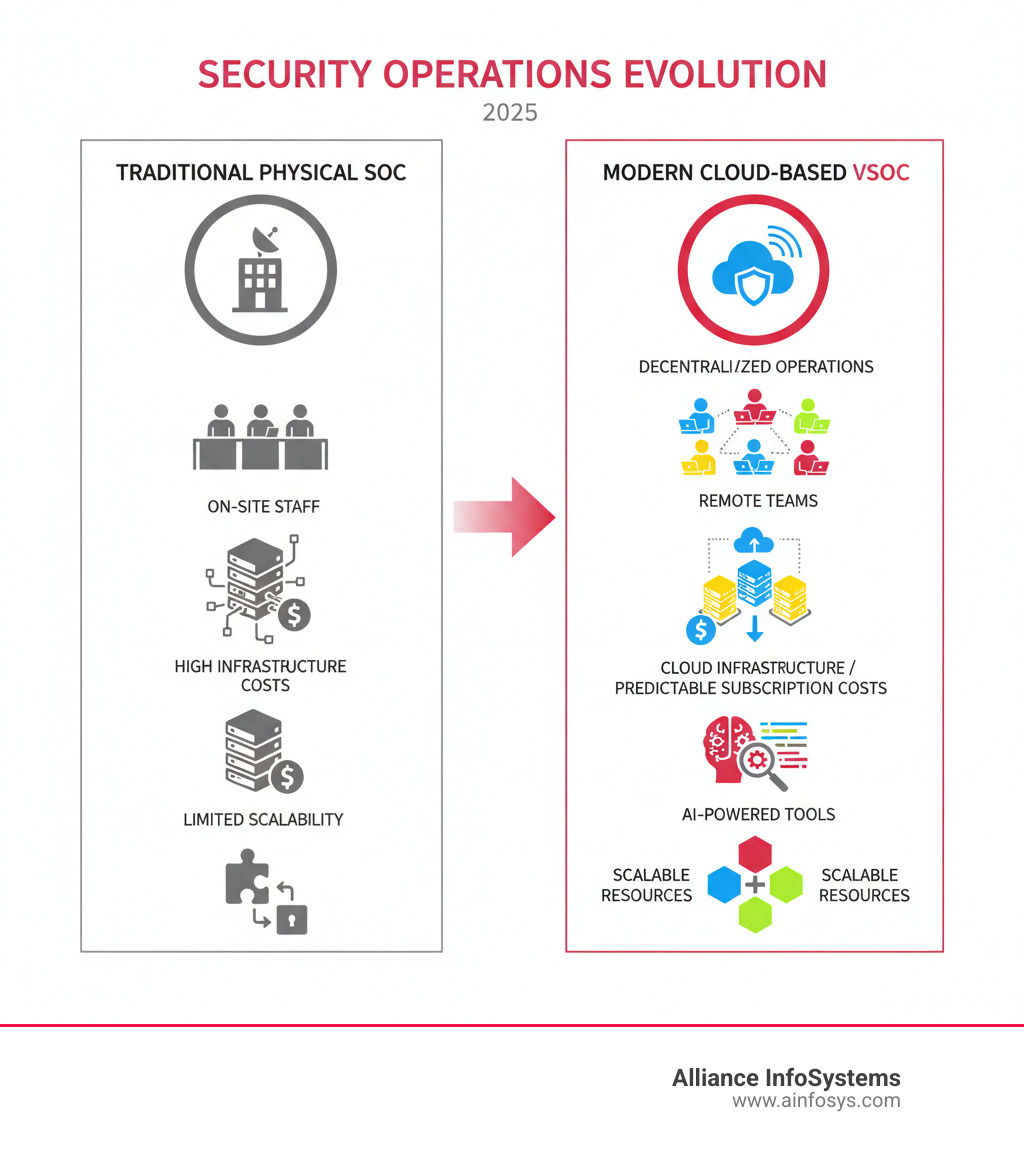
VSOC vs. Traditional SOC: Key Differences
The shift to a virtual security operations center is a fundamental reimagining of security operations.
| Feature | Traditional SOC | Virtual Security Operations Center (VSOC) |
|---|---|---|
| Infrastructure | Physical facility, on-site hardware, centralized | Cloud-based, distributed, remote teams, no physical facility |
| Cost Model | High CapEx (build-out), high OpEx (maintenance) | Subscription-based, lower CapEx, predictable OpEx |
| Staffing | In-house recruitment, training, retention | Outsourced, access to certified global talent, overcomes skills shortage |
| Scalability | Limited, complex to expand | Highly scalable, adapts quickly to changing needs |
| Geographic Location | Centralized, fixed location | Decentralized, global reach for 24/7 coverage |
Traditional SOCs require high upfront costs (CapEx) for a secure facility and hardware, plus significant ongoing operational costs (OpEx) for maintenance, power, and 24/7 staffing. These limitations make the model impractical for most businesses, making the VSOC model’s cost-effectiveness highly appealing.
Understanding Related Concepts: GSOC and mSOC
To clarify some industry terms:
- A Global Security Operations Center (GSOC) was an early model where large companies consolidated global security monitoring into a single, massive physical facility.
- A Modern Security Operations Center (mSOC) is defined by its advanced technology, including AI, machine learning, and automation for intelligent threat detection, risk management, and forensics.
A VSOC is the cloud-enabled evolution of the GSOC concept, making global, 24/7 coverage accessible without the physical building. Importantly, a top-tier VSOC also embodies the capabilities of an mSOC, delivering advanced, AI-driven security as a service. The “modern” aspect is about technological sophistication, not physical location.
The Core Capabilities and Services of a VSOC
A virtual security operations center delivers a comprehensive suite of security services through the cloud, combining advanced technology with human expertise.
At its core is Security Information and Event Management (SIEM) technology, which collects and analyzes log data from across your digital environment. Through log correlation, the system identifies patterns and anomalies that signal a potential threat. VSOC analysts then perform alert triage to separate genuine threats from noise, a process of false positive reduction that saves teams from chasing irrelevant notifications. This focus on actionable intelligence is a key part of how modern Network Security Services Protect Against Modern Cyber Threats.
24/7 Monitoring and Threat Detection
A key advantage of a VSOC is true round-the-clock protection. Using a “follow-the-sun” model, security teams in different time zones provide seamless, continuous surveillance. This combines human intelligence with machine speed. Automated threat detection systems use AI and behavioral monitoring to flag suspicious activity in milliseconds. The technology stack includes Intrusion Detection Systems (IDS) for network traffic and Endpoint Detection and Response (EDR) tools to protect individual devices, creating a comprehensive security net.
Incident Response and Expert Analysis
When an incident occurs, a VSOC executes structured incident handling procedures. Analysts classify the event, assess its impact, and provide clear, actionable remediation recommendations. For complex incidents, the team performs deep-dive analytics and digital forensics to trace the attack’s origin and ensure complete recovery. This process is guided by pre-defined runbooks, or playbooks, that ensure a consistent and effective response to any threat. For a technical overview, this deeper look into VSOC processes offers valuable insights.
The Role of Threat Intelligence and Proactive Hunting
A VSOC moves beyond reactive defense by using threat intelligence feeds from global sources to stay ahead of emerging threats. This intelligence fuels proactive threat hunting, where analysts actively search for hidden indicators of compromise that automated systems might miss. This process often involves developing custom use cases aligned with frameworks like MITRE ATT&CK® to detect sophisticated attacks early. Regular vulnerability scanning and management further strengthens defenses by identifying and closing security gaps before they can be exploited.
Key Benefits: Why Businesses are Adopting the VSOC Model
The adoption of the virtual security operations center model is a strategic shift for smart businesses. A VSOC delivers enterprise-grade protection, access to elite talent, and scalable technology, all while improving an organization’s overall security posture.
Significant Cost Savings and ROI
How does a VSOC contribute to cost savings for an organization?
The financial case for a VSOC is clear. By choosing a virtual model, you eliminate the massive Capital Expenditure (CapEx) of building a physical facility and purchasing hardware. Operational Expenditure (OpEx) is also significantly reduced, as you avoid costs for utilities, maintenance, and equipment upgrades.
Crucially, you bypass the immense hiring and training costs associated with building and retaining a 24/7 in-house security team. A VSOC provides access to certified experts for a predictable subscription fee, minimizing labor and CapEx. This model aligns with the efficiencies gained from other managed services, as detailed in our guide on how to Boost Efficiency with Managed IT Services.
Access to Elite Expertise and Advanced Technology
How do VSOCs leverage technology like AI and cloud infrastructure?
A VSOC is the solution to the cybersecurity skills gap, providing immediate access to a team of dedicated, certified security analysts. These experts are more cost-effective than an in-house team and bring a wealth of experience in threat analysis and incident response.
VSOCs operate on robust cloud infrastructure (like AWS and Azure), enabling instant scalability and resilience. They leverage Artificial Intelligence and Machine Learning for automated threat detection that is up to 10 times faster than traditional methods. Security Orchestration, Automation, and Response (SOAR) platforms further streamline workflows, saving thousands of hours by automating alarm verification and response actions.
Improved Security Posture and Compliance
A virtual security operations center fundamentally improves your organization’s defensive strength. With faster response times, the window for attackers to cause damage shrinks dramatically. A key benefit is the reduction in alert fatigue; expert analysts and AI tools filter out false positives, allowing your internal team to focus on strategic initiatives instead of chasing alerts.
VSOCs are also critical for meeting compliance requirements like GDPR, HIPAA, and PCI DSS. They provide the 24/7 SIEM monitoring, audit support, and reporting needed to demonstrate compliance and avoid penalties. This continuous oversight ensures you are always prepared for an audit. To learn more about compliance certifications, explore our discussion on SOC 2 Certified MSPs.
Implementing a VSOC: Onboarding and Choosing a Provider
Implementing a virtual security operations center improves your existing IT team, it doesn’t replace it. A VSOC acts as an extension, lifting the burden of 24/7 monitoring so your staff can focus on strategic projects. Success depends on choosing the right partner and establishing a clear partnership model defined by Service Level Agreements (SLAs) and open communication.
The Typical Onboarding and Integration Process
What is the typical process for onboarding and integrating a VSOC service?
A smooth transition to a VSOC typically follows these steps:
- Assessment & Planning – The provider learns your environment, systems, and compliance needs to create a custom roadmap.
- Technology & SIEM Integration – Your existing SIEM (or a newly deployed one) is connected to the VSOC infrastructure, and secure data feeds are configured.
- Runbook & Process Development – You collaborate with the provider to create custom incident response procedures and escalation protocols.
- Pilot Operations – The service is tested in a controlled pilot phase to fine-tune configurations before full deployment.
- Full Implementation & Optimization – The service goes live, with continuous optimization to adapt to evolving threats and business needs.
How to Choose the Right virtual security operations center Provider
How can businesses choose the right VSOC provider for their needs?
Not all VSOC providers are equal. Look for:
- Flexible Service Tiers: Ensure the provider offers customizable packages (e.g., Essentials, Plus, Premium) that can scale with your business.
- Clear Reporting: The provider should deliver actionable reports on threats, responses, and vulnerabilities, not just technical jargon.
- Proven Expertise: Look for certified analysts, industry accreditations, and a strong track record.
- Team Integration: The provider should act as a partner, with clear communication protocols and collaboration tools that empower your existing IT staff.
- Transparency: A trustworthy provider is upfront about processes, technology, and pricing. For more tips, see our guide on 7 Factors for Choosing IT Cybersecurity Services.
Potential Challenges of a virtual security operations center
While powerful, outsourcing security requires awareness of potential challenges:
- Loss of direct control: Mitigate this by choosing a transparent provider who offers regular reporting and collaborative decision-making.
- Communication gaps: Ensure crystal-clear communication channels and escalation protocols are established from the start.
- Data privacy concerns: Vet providers for robust data handling practices, including end-to-end encryption and regular security audits.
- Technology dependencies: Ask about redundancy and disaster recovery plans to ensure service resilience.
- Vetting providers: Thoroughly review SLAs, ask for references, and scrutinize case studies before signing a contract.
By addressing these points, you can maximize the benefits of a VSOC. For more on our approach, explore our Managed Security services.
Frequently Asked Questions about Virtual SOCs
How does a VSOC complement an existing IT team?
How do VSOCs complement or augment an organization’s existing IT or security teams?
A virtual security operations center acts as a force multiplier for your existing IT team, not a replacement. It handles the relentless, 24/7 task of security monitoring and alert triage, freeing your internal staff from alert fatigue. This allows your team, who holds irreplaceable knowledge of your business operations, to focus on strategic initiatives that drive growth. The VSOC provides specialized security expertise that is difficult and expensive to maintain in-house, creating a partnership where each team plays to its strengths.
What technologies do VSOCs typically use?
A VSOC leverages a sophisticated technology stack that includes:
- Security Information and Event Management (SIEM): Platforms like Splunk, Sentinel, or QRadar to collect and analyze security data.
- Security Orchestration, Automation, and Response (SOAR): Tools to automate and streamline incident response workflows.
- Endpoint Detection and Response (EDR): Solutions to monitor and protect individual devices like laptops and servers.
- Threat Intelligence Platforms (TIPs): Systems that aggregate global threat data to provide context and enable proactive hunting.
This entire stack is typically built on resilient cloud infrastructure (like AWS or Azure) and connected via secure communication tools.
Is a VSOC suitable for small and medium-sized businesses (SMBs)?
Yes, a virtual security operations center is an ideal solution for SMBs. Building an in-house SOC is prohibitively expensive due to infrastructure, software, and staffing costs. A VSOC provides access to the same enterprise-grade tools and certified experts used by large corporations but through a cost-effective, predictable subscription model. As one analysis notes, “virtual SOCs offer a cost-effective solution suitable for businesses of any size and budget.” It removes resource limitations as a barrier to achieving a robust, 24/7 security posture.
Conclusion
In a digital world of changing threats, a robust security strategy is essential for survival. A virtual security operations center offers a modern, agile solution that brings enterprise-grade protection within reach for organizations of all sizes.
A VSOC eliminates massive infrastructure costs, provides instant access to certified security experts, and delivers 24/7 protection powered by cutting-edge AI and cloud technology. With continuous monitoring, rapid incident response, and proactive threat hunting, you dramatically strengthen your security posture and simplify compliance with regulations like GDPR, HIPAA, and PCI DSS.
For businesses in Maryland and beyond, the question is how to implement effective security without breaking the bank. Alliance InfoSystems has over 20 years of experience providing flexible, customized security solutions that fit unique business needs and budgets. We build partnerships, augmenting your team so they can focus on growing your business.
The threat landscape will continue to change, but you don’t have to face it alone. Strengthen your defenses with our Managed Security services and find how Alliance InfoSystems can protect what you’ve worked so hard to build.