What is Network Security Management?
Understanding network security management is key to keeping your business safe online. It’s the practice of protecting your organization’s network infrastructure and data from online dangers using a mix of policies, processes, and technologies. The goal is to prevent unauthorized access and data breaches, ensuring your network remains usable, reliable, and your data confidential.
While keeping up with ever-changing threats can feel overwhelming, securing your network is a core part of running your business and protecting your reputation.
Why It’s More Critical Than Ever for Enterprises
Cyber threats are getting smarter and more frequent, making the risks for businesses higher than ever.
-
The attack surface is expanding. You’re not just protecting computers, but all connected devices, including the 90 percent of corporate applications that may soon be on personal mobile devices.
-
A single security gap can lead to financial loss, reputational damage, and regulatory fines. For example, Gartner predicted that 99% of firewall breaches through 2023 would be caused by simple misconfigurations, not technology failure.
-
Effective network security management avoids these pitfalls. It protects your data, ensures operational continuity, and helps you meet compliance rules. It’s a layered defense for your business assets.
At Alliance InfoSystems, we understand that safeguarding your network is about more than just technology; it’s about peace of mind. We’ve been helping businesses in Maryland and beyond steer the complexities of IT management and security since 2004, offering flexible, customized, and cost-efficient solutions. We believe in being proactive, not just reactive, when it comes to cybersecurity.
Want to dive deeper into protecting your digital assets? You can find More info about network security on our site. Cyberthreats are on the rise, and a solid strategy is essential for your business continuity.
The Core Components of a Robust Security Strategy
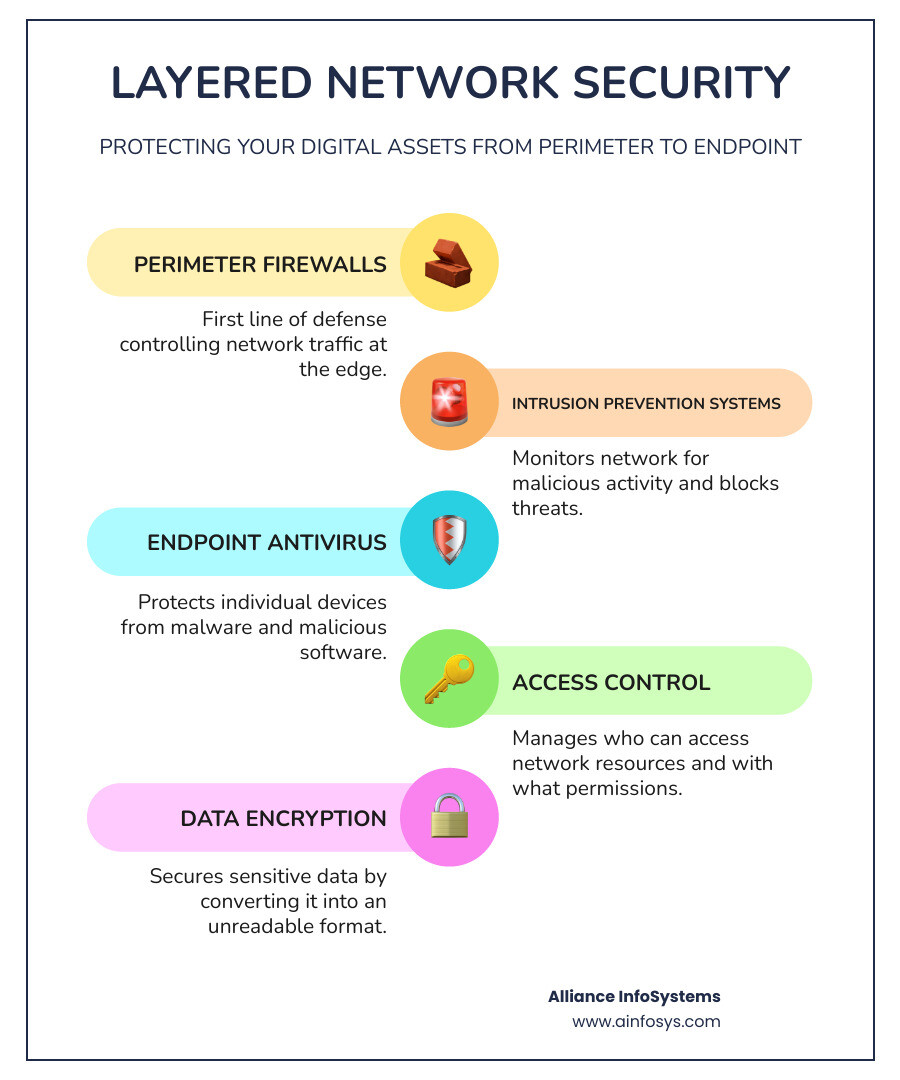
Building a strong defense requires many layers of protection working together. An effective network security management strategy combines hardware, software, smart policies, and the human element to create a proactive and secure posture for your business.
Foundational Hardware and Software
These are the digital guards and alarm systems of your network, forming the first line of defense.
-
Firewalls: Act as a digital bouncer, monitoring traffic and allowing only approved data to pass based on set rules. Modern firewalls offer advanced threat detection, but proper configuration is critical to avoid leaving a door open. Learn How to avoid firewall mistakes.
-
Unified Threat Management (UTM): Combines multiple security features like firewalls, intrusion prevention, and antivirus into a single device, simplifying management.
-
Intrusion Prevention Systems (IPS): Actively patrol your network to detect and block known and suspected threats before they cause harm, sometimes offering “virtual patching” for new vulnerabilities.
-
Antivirus and Sandboxing: Antivirus software blocks known malware, while sandboxing provides a safe, isolated environment to test suspicious files without risking your live network.
-
VPNs (Virtual Private Networks): Create a secure, encrypted tunnel for remote users, ensuring data remains private as it travels to your company network.
-
Network Access Control (NAC): Acts as a gatekeeper, ensuring only authorized and compliant devices can connect. Non-compliant devices can be quarantined until fixed.
-
Web Filtering and Secure Gateways: Control access to websites, block web-based threats, and enforce your company’s internet use policies. A secure gateway is a checkpoint for all web traffic.
People and Policies: The Human Layer
Technology is powerful, but people are often your strongest security asset—or weakest link. Clear policies and training are essential.
-
Security Policies: The rulebook for your digital world, defining how data is handled and what constitutes acceptable use.
-
Access Control Policies: Dictate who can access specific files or systems, guided by the principle of “least privilege” (granting only the minimum access needed).
-
Acceptable Use Policy: Spells out how employees can use company network resources to prevent misuse that could introduce risks.
-
Incident Response Plan: A playbook for a swift, coordinated response to a security incident, minimizing damage and speeding up recovery.
-
Employee Training and Security Awareness: Regular training and phishing simulations are vital to empower your team against threats like human error. Let us help you Keep employees cyber aware.
-
Role-Based Access Control (RBAC): Simplifies access management by assigning permissions based on job roles, reducing the risk of users gaining excessive privileges over time.
Centralized Management and Monitoring
Managing many separate security tools is inefficient and prone to errors. Centralization brings harmony and visibility.
-
Single-Pane-of-Glass Management: Allows you to manage all security tools and policies from one unified control panel, simplifying operations.
-
SIEM (Security Information and Event Management): Collects and analyzes activity logs from across your network in real-time to identify threats and send alerts. It’s invaluable for threat detection and compliance. Curious? Check out What is a Managed SOC? or learn about What is SOCaaS?.
-
Log Management: Ensures all security logs are collected, stored securely, and retained as needed for compliance and incident investigation.
-
Real-time Visibility: Provides instant insights into network behavior and potential threats as they happen, enabling faster reactions.
-
Automation: Automating routine security tasks like policy application and vulnerability scanning reduces human error and frees up your IT team.
-
Threat Hunting: A proactive approach where security experts actively search for hidden threats that may have bypassed automated defenses.
8 Actionable Steps to Improve Your Network Security Management
An effective network security management strategy is an ongoing journey, not a one-time fix. It requires regular care and a proactive approach to build resilience against changing cyber threats. Here are six actionable steps to strengthen your organization’s cybersecurity posture.
Step 1: Organize and Inventory All Network Assets
You can’t protect what you don’t know. The first step is to get a clear picture of everything connected to your network. This means thorough asset management to identify and track all physical devices (servers, PCs, printers, IoT), virtual assets, and cloud resources. Clear network diagrams are also essential to visualize traffic flow and identify weak points. For a deeper dive, see our guide on how to secure your IT infrastructure.
Step 2: Fortify Access Control with Strong Authentication
Once you know what to protect, you must control who gets in. Start with the Least Privilege Principle, giving users only the minimum access needed for their jobs. A Zero Trust model, which means “never trust, always verify,” is also highly effective. Enforce strong passwords, but the real game-changer is Multi-Factor Authentication (MFA), which can block 99.9% of account attacks by requiring a second form of verification. Learn more about Multi-factor authentication and find More on Multifactor Authentication on our site. Finally, conduct regular user access reviews and immediately disable inactive accounts to close potential back doors.
Step 3: Implement a Proactive Vulnerability Management Program
Attackers look for open windows—vulnerabilities in your systems. A proactive program finds and seals them before they can be exploited. This includes consistent patch management to keep all software and firmware updated. Find out What is a patch?. Regularly use vulnerability scanning to find known weaknesses and penetration testing (ethical hacking) to uncover deeper issues. You must also be prepared for Zero-day threats (brand-new vulnerabilities) with strong detection and response capabilities. Even major systems can be at risk, so know how to Protect against iOS vulnerabilities.
Step 4: Deploy and Manage Endpoint Security
Endpoints (laptops, desktops, mobile devices) are prime targets for cybercriminals. Start with foundational Antivirus software and layer on Endpoint Detection and Response (EDR) solutions to continuously monitor for suspicious activity. Use Data Loss Prevention (DLP) tools to block sensitive data from leaving your control. For personal devices (BYOD), Mobile Device Management (MDM) solutions are essential for enforcing security policies. Learn more about What is MDM?.
Step 5: Harden Your Data Protection and Recovery Plans
How quickly could your business recover from a disaster or cyberattack? Protecting your data is non-negotiable. Use data encryption for data both at rest (stored) and in transit (moving across networks). Implement data classification to apply the right level of protection based on sensitivity. Set up regular backups in multiple secure locations—your best defense against ransomware. We offer comprehensive Data Backup & Recovery services. Define your Recovery Point Objective (RPO) (how much data you can lose) and your Recovery Time Objective (RTO) (how quickly you must recover), and test your Disaster Recovery Plan regularly. Understanding Disaster recovery statistics highlights why this is vital.
Step 6: Establish Clear Security Policies and Procedures
Good intentions aren’t enough; you need documented rules and processes. This involves creating thorough security documentation, a consistent employee training schedule, and clear emergency protocols. Implement change management with audit trails to prevent misconfigurations. Establish key policies, including Acceptable Use, Password, Incident Response, Data Classification, Remote Access, Information Security, and BYOD. For comprehensive guidance, refer to the Guidance from the SANS Institute or our Top 10 cyber security practices.
Overcoming Common Problems in Network Security
Even with the best tools, network security management presents challenges. Modern networks are complex, threats evolve, and human error is always a factor. Understanding these common problems is the first step to building a more resilient defense.
The Challenge of Misconfigurations and Policy Bloat
Surprisingly, most breaches aren’t due to technology failure. Gartner predicted that 99% of firewall breaches through 2023 would be caused by misconfigurations. In complex networks, a simple oversight can create a major security hole. Over time, policies can become outdated and conflicting (“policy bloat”), making security difficult to manage and increasing the risk of human error. The solution is automation, which can check rules, spot inconsistencies, and apply policies accurately, strengthening your security posture. This is a key part of how network security services protect you.
The Role of Centralized Network Security Management
Managing security across hybrid and multi-cloud environments with tools from different vendors is a major headache. A centralized solution provides a single control panel to configure and manage security policies for all your tools. This leads to simplified administration, consistent policy enforcement, and significant cost savings. By streamlining operations, centralized network security management reduces complexity and boosts efficiency, a powerful way to improve enterprise information security.
Keeping Pace with Evolving Cyber Threats
Cybercriminals constantly refine their tactics, so your defenses must be dynamic. Common threats include:
- Ransomware: Encrypts your data and demands payment. Learn 7 ways to avoid ransomware in your business.
- Phishing: Tricks employees into revealing sensitive information. It’s crucial to know 5 simple ways to avoid malicious emails.
- Malware: Malicious software designed to disrupt or gain unauthorized access.
- Insider threats: Misuse of access by employees, contractors, or partners.
- DDoS attacks: Flood your systems with traffic, making them unavailable.
Effective network security management requires continuous monitoring, real-time threat intelligence, and the flexibility to adapt your security controls to new dangers.
Frequently Asked Questions about Network Security Management
When we work with businesses to strengthen their cybersecurity, certain questions come up time and again. Let’s tackle the most common concerns about network security management.
What types of threats does network security management help prevent?
Effective network security management protects against a wide range of threats, including:
- Malware: Viruses, worms, and Trojans designed to cause damage or steal data.
- Ransomware: Attacks that lock your files and demand payment for their release.
- Phishing attacks: Fake emails and websites designed to trick users into revealing credentials.
- Insider threats: Malicious or accidental actions by employees or partners with legitimate access.
- Data exfiltration: The unauthorized transfer of sensitive data from your network.
- Denial-of-Service (DoS) attacks: Attempts to make your network unavailable to legitimate users by overwhelming it with traffic.
- Man-in-the-middle attacks: Eavesdropping on communications to steal or alter information.
Want to learn more about the biggest threats out there? Check out our detailed whitepaper on the 2 most dangerous cyber threats in the cyber wild west.
How does cloud computing impact network security management?
Cloud computing introduces new complexities to network security management. The biggest change is the shared responsibility model, where the cloud provider secures the infrastructure, but you are responsible for securing your data, applications, and configurations within the cloud. Key challenges include:
- Cloud misconfigurations: Simple errors in cloud settings can easily expose sensitive data to the public internet.
- Data breaches: Investigating and remediating breaches can be more complex in distributed cloud environments.
- Compliance: You must ensure your cloud setup meets the same regulatory requirements as your on-premises systems.
- Cloud-specific security tools: Traditional tools may not be effective, requiring solutions like cloud access security brokers (CASBs).
- Consistent policies: Maintaining consistent security across hybrid environments (on-premises and cloud) is crucial to reduce your attack surface.
How often should we review our network security policies?
Network security policies are not “set and forget.” They require regular attention to remain effective. We recommend a comprehensive annual review at a minimum. However, you should also review policies at other key times:
- After any security incident to address gaps that were exploited.
- When you adopt new technologies to account for new risks.
- When regulatory requirements change to ensure ongoing compliance.
The best practice is continuous monitoring and improvement, making small adjustments as your business and the threat landscape evolve. The NIST guidance on continuous monitoring provides an excellent framework for this approach.
Conclusion: Partner with Experts for a Resilient Security Posture
Effective network security management is essential for keeping your business safe. It requires a proactive, layered defense that is constantly improving. From hardware and software to policies and training, every piece plays a vital role in your overall protection.
Navigating these complexities can be daunting, but you don’t have to do it alone.
Our team at Alliance InfoSystems has helped businesses build and maintain secure networks since 2004. With over 20 years of experience, we understand the challenges faced by organizations in Maryland and beyond. We offer flexible, customized, and cost-efficient solutions custom to your specific needs.
Partnering with an expert provides access to cutting-edge knowledge, best practices, and the peace of mind that comes from knowing your network is protected. We can help you craft a strategic plan that defends against today’s threats and adapts to tomorrow’s challenges.
Ready to strengthen your defenses? We’re here to help! Learn how we can Partner with us for expert cloud and virtualization services or explore how to Find the best IT security service providers to keep your network safe.